Security and Robustness for Intermittent Computing Using Cross-Layer Post-CMOS Approaches
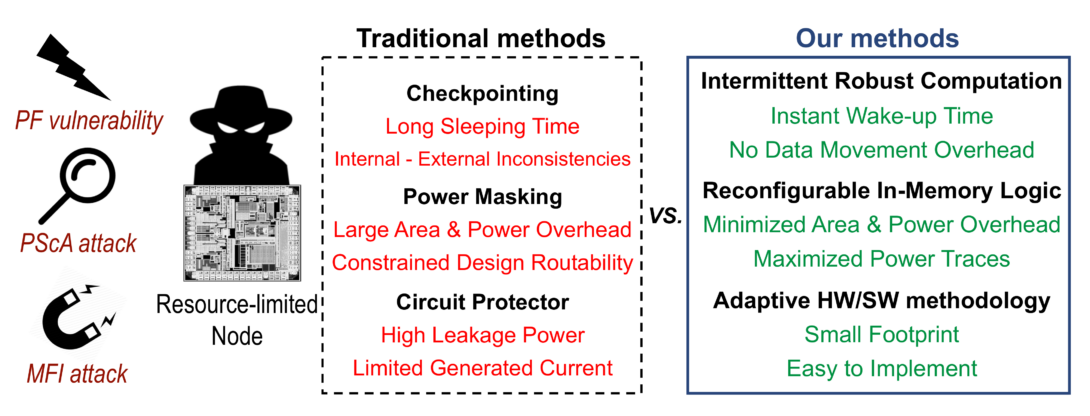
The realization of resource-limited, normally-off energy harvesting devices has impacted a wide range of Internet of Things (IoT) applications such as wearable devices, remote sensing, and industrial systems. Nevertheless, these devices are typically exposed to various existing and new vulnerabilities, including physical attacks, such as side-channels and magnetic attacks, unanticipated power outages and power failures, and other unique vulnerabilities. Exploiting these vulnerabilities could lead to irreparable damage to property and lives because of the large number of connected nodes/devices. The available defense schemes against these attacks either have high overheads, which make them inapplicable to resource-constrained nodes, or incomplete.
Security and Robustness for Intermittent Computing Using Cross-Layer Post-CMOS Approaches Image
To address these shortcomings, our research aims to develop comprehensive yet lightweight security strategies. Specifically, our objective is to ensure secure, intermittent-robust computation for these resource-constrained, normally-off computing nodes. We plan to achieve this by leveraging emerging, non-volatile, spin-based devices to construct reconfigurable logic circuits that are both lightweight and secure. Our approach centers on ensuring that computations can continue robustly even in the face of various types of attacks. This is made possible by storing intermediate computational states within non-volatile (NV) devices. Additionally, we aim to innovate new techniques that synergize circuit design, architectural paradigms, and algorithmic methods. These new techniques not only bolster the system’s resilience against attacks but also minimize the resource overhead, making the solution both effective and efficient. By achieving this objective, we aspire to set a new benchmark in the realm of secure computing for IoT applications, thereby ensuring a safer and more reliable digital future.
Supported by NSF.
Collaborators: UTEXAS, UCLA